A massive ransomware attack struck on a global scale late last week, hijacking around 300,000 computers in at least 150 countries. The virus, known as WannaCry, shut down hundreds of thousands of businesses around the world, including the UK’s National Health Service – and many countries are still only just recovering.
At Cymax, we were fortunate enough to apply proactive preventative maintenance measures to our clients’ systems several weeks ago, which in this instance, provided the necessary protection against the WannaCry ransomware.
But this doesn’t mean you should let your guard down. Ransomware is now a billion dollar industry and the payload of choice for many malicious email campaigns and exploit kits across the globe, with 638 million instances of ransomware reported in 2016 alone.
WannaCry was a huge wake-up call to remind us that in an age where we are now more reliant on technology than ever before, it’s essential that we always remain vigilant online.
WannaCry Explained
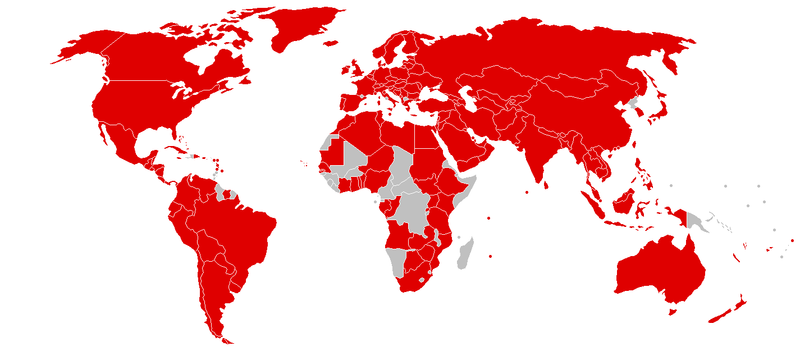
The way the WannaCry ransomware worked was by infecting computers with a virus sent through email. Using fake invoices, job offers and other lures with a .zip file that initiated the virus when opened, WannaCry was able to spread with unthinkable speed – as you can see by this map of all the countries initially affected by the malware.
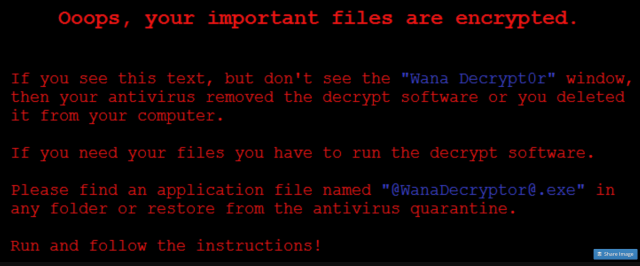
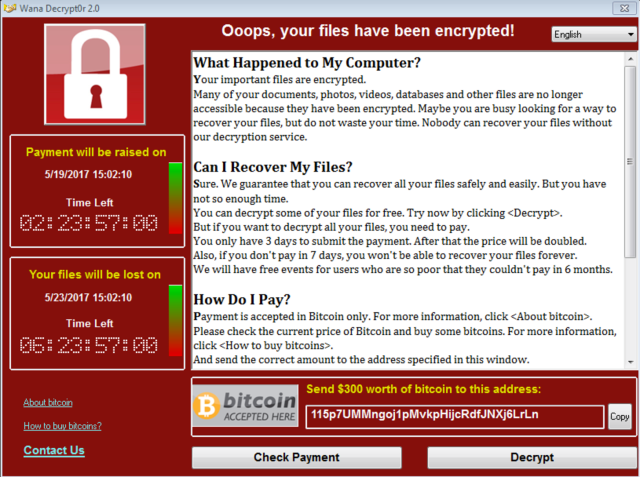
Once a computer was infected, the virus exploited a vulnerability in some older versions of Windows to spread over the network (over 98% of victims were using Windows 7). From there, it encrypted files on the hijacked computers so that users couldn’t access them, and ransom notes appeared on victims’ screens demanding bitcoin payments in return for the release of their files.
Source
Source
Since the attack began, the three bitcoin wallets set up to collect ransom payments have received 296 payments totalling 48.86359565 BTC ($99,448 USD).
What makes this particular ransomware attack even more complicated is the fact that it’s suspected that the WannaCry malware came from a cache of hacking tools that may have been stolen from the US National Security Agency and leaked on the internet. The tools include an exploit called EternalBlue which makes it easy to hijack older, unpatched Windows systems – something that may have drawn hackers to target these systems in the first place.
Proactive Measures
Microsoft released a security update on March 14 to patch the vulnerability in their system that was exploited by WannaCry. Fortunately, we had already proactively applied these patches to our clients’ systems shortly after as part of our preventative maintenance, and none of them were affected as a result.
When the attack hit, Cymax’s Crypto Task Force worked tirelessly and diligently to ensure all systems were quality assured and the necessary patch was installed and verified.
Unfortunately, when it comes to ransomware, we can only make the environment as secure and safe as the measures and tools that we have available. We were fortunate enough in this instance, that all of our proactive measures held true, and we are continually refining our processes to keep your system secure no matter what.
At Cymax, our clients’ security is our number one priority, and we partner with industry leaders to better predict what’s coming and to proactively prepare for it. But while we have to get it right every time, hackers only have to get it right once – so it’s very important that you never let your guard down.
What You Can Do to Protect Yourself
Ransomware is unpredictable and can be immensely damaging, but there are simple steps you can take to protect yourself and your business.
- Be cautious about opening email attachments, even from people you know.This doesn’t just apply to .zip files either – cyber criminals can quite easily change the extension of a malicious file to .doc or some other seemingly harmless file type. If you’re not sure about the legitimacy of an attachment, always contact the sender to find out.
- Don’t click on any hyperlinks in emails unless you’re 100% sure they’re safe.Just like with attachments, links in the body of emails can also be infected. If you have any doubt, it’s safer to simply delete the email if you don’t know the sender, or contact them if you do.
- Make regular, offsite backups.This is something you should always be doing anyway, but with the threat of ransomware now so prevalent, it’s especially important to have a backup of important files somewhere safe.
- Partner with an internet security leader.At Cymax, we take proactive, preventative steps to ensure your system is protected and as secure as possible – even before an event like this happens.


